Diamond Cut Forensics Audio Laboratory is a comprehensive application made for audio restoration and enhancement. Mostly developed for expert users, it contains a wide range of filters and effects.
Introduction to computer forensics
Computer forensics deals with the collection of evidence from digital media, such as desktops, mobile devices, cloud computing and IoT devices. This evidence can be used as part of incident remediation activities or to support law enforcement activities.
The best computer forensics tools
This forensic video enhancement software is developed for Windows users and can also be used by investigators and law enforcement officials. This free, professional grade video enhancement tool comes without any ads to distract you and a detailed information guide for all kinds of assistance to get the job done faster. Forensic Explorer 3.6.2.5582 is free to download from our software library. This tool was originally produced by GetData Forensics. The program lies within Education Tools, more precisely Science Tools. The most frequent installation filename for the software is: ForensicExplorer.exe. The most popular versions of the program are 3.6, 3.5 and 3.4. Forensics free download - Excel Power Expander, Access Forensics, QuickBooks Forensics, and many more programs Join or Sign In Sign in to add and modify your software Sign in with FacebookSign in. Our Heritage: Best in Class. Proven in Courts. Guidance created the category for digital investigation software with EnCase Forensic in 1998. EnCase has maintained its reputation as the gold standard in criminal investigations and was named the Best Computer Forensic Solution.
Digital evidence can exist on a number of different platforms and in many different forms. Forensic investigation often includes analysis of files, emails, network activity and other potential artifacts and sources of clues to the scope, impact and attribution of an incident.
Due to the wide variety of potential data sources, digital forensics tools often have different specialties. This list outlines some of the most common and widely used tools for accomplishing different parts of a computer forensics investigation.
Disk analysis: Autopsy/The Sleuth Kit
Autopsy and The Sleuth Kit are likely the most well-known forensics toolkits in existence. The Sleuth Kit is a command-line tool that performs forensic analysis of forensic images of hard drives and smartphones. Autopsy is a GUI-based system that uses The Sleuth Kit behind the scenes.
The tools are designed with a modular and plug-in architecture that makes it possible for users to easily incorporate additional functionality. Both tools are free and open-source, but commercial support and training are available as well.
Read more about Autopsy and The Sleuth Kit here.
Image creation: FTK Imager
Autopsy and The Sleuth Kit are designed to examine disk images of hard drives, smart phones and so on. The benefit of analyzing an image (rather than a live drive) is that the use of an image allows the investigator to prove that they have not made any modifications to the drive that could affect the forensic results.
Autopsy does not have image creation functionality, so another tool needs to be used. While the majority of the AccessData Forensics Toolkit items are paid tools, its FTK Imager is a free product. This can be used to create disk images that can then be analyzed using Autopsy/The Sleuth Kit.
More information about FTK Imager is available here.
Memory forensics: Volatility
Tools like The Sleuth Kit focus on the hard drive, but this is not the only place where forensic data and artifacts can be stored on a machine. Important forensic information can be stored in RAM, and this volatile memory must be collected quickly and carefully to be forensically valid and useful.
Volatility is the most well-known and popular tool for analysis of volatile memory. Like The Sleuth Kit, Volatility is free, open-source and supports third-party plugins. In fact, the Volatility Foundation holds an annual contest for users to develop the most useful and innovative extension to the framework.
Learn more about Volatility here.
Windows Registry analysis: Registry Recon
The Windows Registry acts as a database of configuration information for the Windows OS and the applications running on it. These applications can store a variety of different data in the registry, and the registry is one of the common locations where malware deploys persistence mechanisms.
It is possible to open and view the Windows registry via the built-in Windows application regedit, and registry analysis is built into some forensics platforms. However, specialized tools like Registry Recon are available as well. Registry Recon is a commercial tool that is designed to rebuild Windows registries from a forensic image and includes the ability to rebuild deleted parts of the registry based upon analysis of unallocated memory space.
For more information about Registry Recon, visit here.
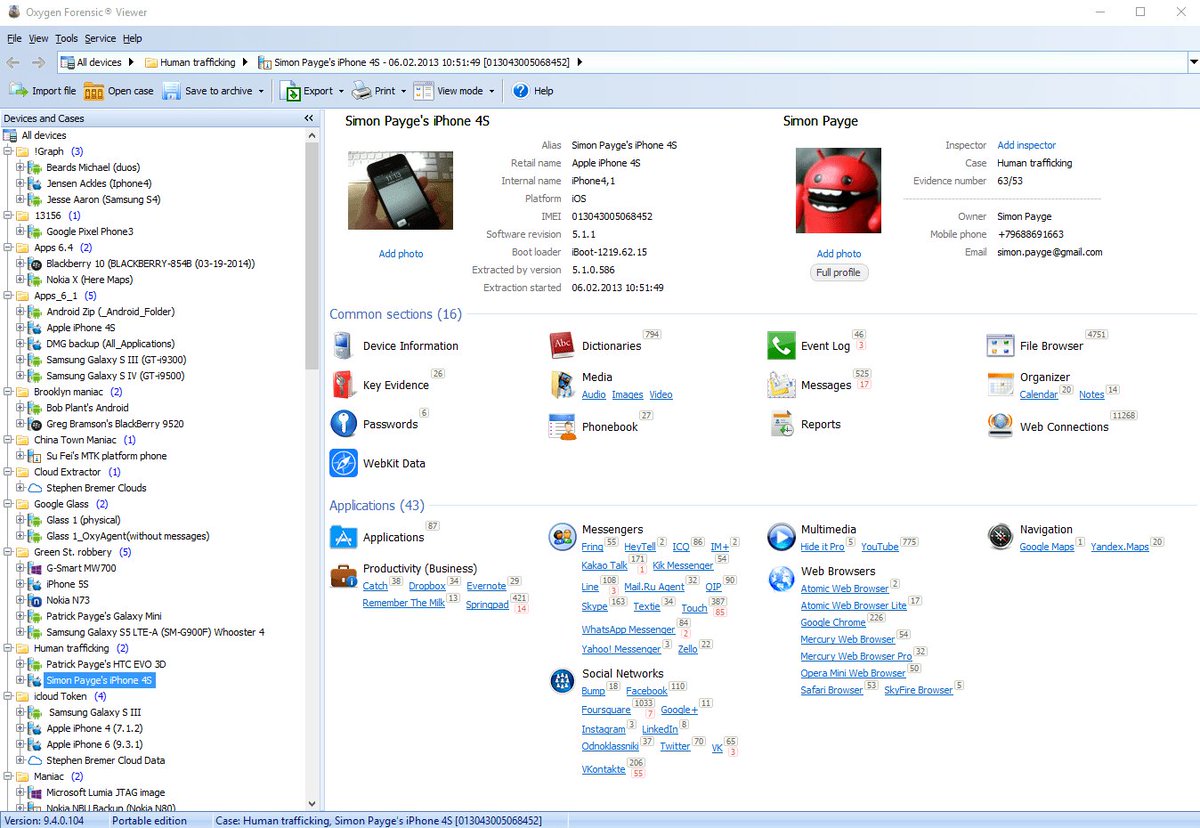
Mobile forensics: Cellebrite UFED
Mobile adoption is constantly growing, and many organizations allow employees to use these devices at work either via BYOD programs or corporate-owned devices. Additionally, these devices are a growing target of cyberattacks, such as phishing, making them a likely source of valuable forensic information.

With the growing importance of mobile forensics, a mobile-focused forensics tool might be a useful acquisition. Cellebrite UFED is widely regarded as the best commercial tool for mobile forensics. It supports a number of different platforms (not just mobile devices) and boasts exclusive methods and tools for mobile device analysis.
Read more about Cellebrite UFED here.
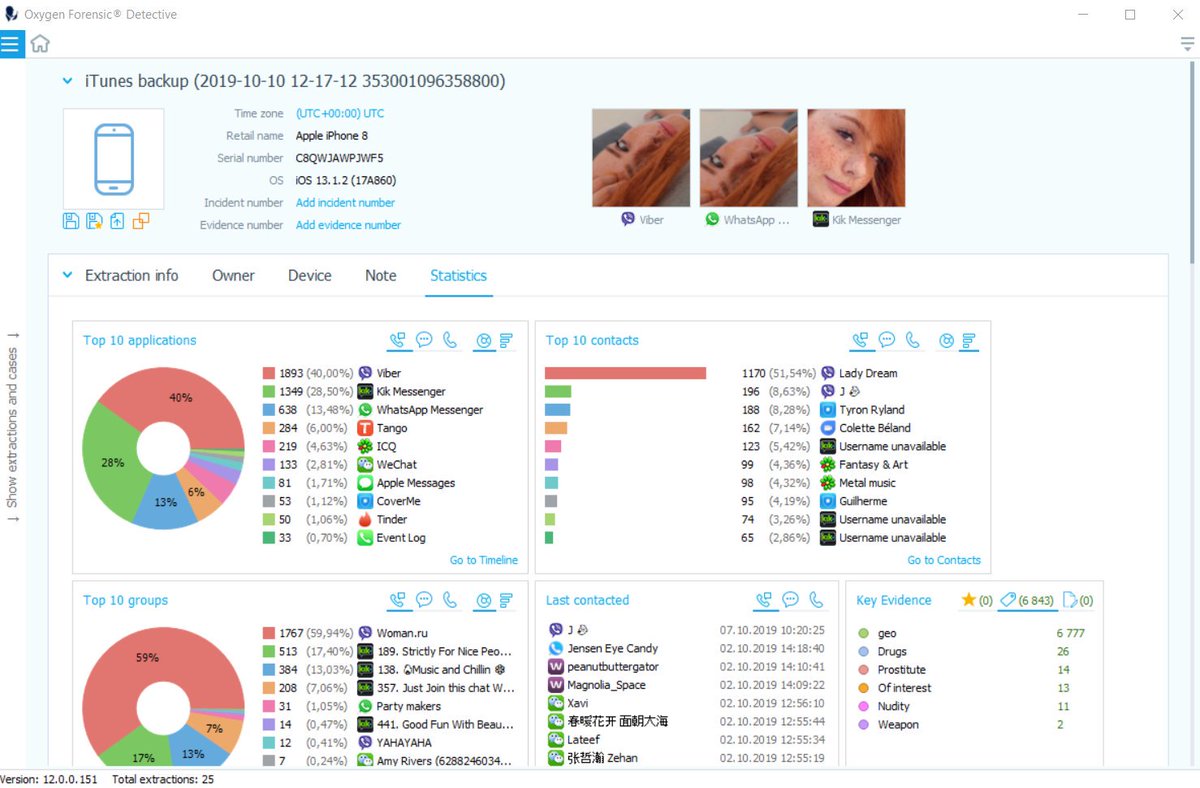
Network analysis: Wireshark

Many forensics tools focus on the endpoint, but this is not the only source of useful data in a forensics investigation. Most cyberattacks occur over the network, and analysis of network traffic captures can help with the identification of malware and provide access to data that may have already been deleted and overwritten on the endpoint.
For network traffic analysis, Wireshark is the most popular and widely-used tool. Wireshark is free and open-source, offers dissectors for many different types of network traffic, has a clear and easy-to-use GUI for traffic analysis and includes a wide range of functionality under the hood. It supports live traffic capture or can ingest network capture files for analysis.
Learn more about Wireshark here.
Linux distributions: CAINE
Many of the tools presented here (and many other digital forensics tools besides them) are free and open-source. While this makes them easy to acquire, installation and configuration can be complex. To simplify this process, a number of different Linux digital forensics distributions are available as virtual machines. These VMs include a number of tools pre-installed and preconfigured.
The Computer Aided Investigative Environment (CAINE) is one example of such a tool. This Linux distribution includes many of the most widely used computer forensics tools and may include third-party plugins for tools like Autopsy.
Learn more about CAINE here.
Forensic software, free download
Getting started with computer forensics
These seven tools don’t even scratch the surface of the tools available for digital forensics. Offerings range from free and open-source scripts designed to accomplish a single task to massive, commercial forensics platforms.
Due to the wide range of potential tools, a good starting point is trying out a Linux forensics distribution like CAINE. This provides access to a range of free tools without requiring any purchases or configuration.
Computer Forensic Software Free
- Overview
- Tips & Tricks
- Uninstall Instruction
- FAQ
Forensic Toolkit Description
TK is a court-accepted digital investigations platform that is built for speed, analytics and enterprise-class scalability. Known for its intuitive interface, email analysis, customizable data views and stability, FTK lays the framework for seamless expansion, so your computer forensics solution can grow with your organization's needs.Features
- Forensic Toolkit Free & Safe Download!
- Forensic Toolkit Latest Version!
- Works with All Windows versions
- Users choice!
Disclaimer
Forensic Toolkit is a product developed by Accessdata Group. This site is not directly affiliated with Accessdata Group. All trademarks, registered trademarks, product names and company names or logos mentioned herein are the property of their respective owners.
All informations about programs or games on this website have been found in open sources on the Internet. All programs and games not hosted on our site. When visitor click 'Download now' button files will downloading directly from official sources(owners sites). QP Download is strongly against the piracy, we do not support any manifestation of piracy. If you think that app/game you own the copyrights is listed on our website and you want to remove it, please contact us. We are DMCA-compliant and gladly to work with you. Please find the DMCA / Removal Request below.
DMCA / REMOVAL REQUEST
Please include the following information in your claim request:
- Identification of the copyrighted work that you claim has been infringed;
- An exact description of where the material about which you complain is located within the QPDownload.com;
- Your full address, phone number, and email address;
- A statement by you that you have a good-faith belief that the disputed use is not authorized by the copyright owner, its agent, or the law;
- A statement by you, made under penalty of perjury, that the above information in your notice is accurate and that you are the owner of the copyright interest involved or are authorized to act on behalf of that owner;
- Your electronic or physical signature.
You may send an email to support [at] qpdownload.com for all DMCA / Removal Requests.
You can find a lot of useful information about the different software on our QP Download Blog page.
Latest Posts:
How to uninstall Forensic Toolkit?
How do I uninstall Forensic Toolkit in Windows Vista / Windows 7 / Windows 8?
- Click 'Start'
- Click on 'Control Panel'
- Under Programs click the Uninstall a Program link.
- Select 'Forensic Toolkit' and right click, then select Uninstall/Change.
- Click 'Yes' to confirm the uninstallation.
How do I uninstall Forensic Toolkit in Windows XP?
- Click 'Start'
- Click on 'Control Panel'
- Click the Add or Remove Programs icon.
- Click on 'Forensic Toolkit', then click 'Remove/Uninstall.'
- Click 'Yes' to confirm the uninstallation.
How do I uninstall Forensic Toolkit in Windows 95, 98, Me, NT, 2000?
- Click 'Start'
- Click on 'Control Panel'
- Double-click the 'Add/Remove Programs' icon.
- Select 'Forensic Toolkit' and right click, then select Uninstall/Change.
- Click 'Yes' to confirm the uninstallation.
Frequently Asked Questions
How much does it cost to download Forensic Toolkit?
Nothing! Download Forensic Toolkit from official sites for free using QPDownload.com. Additional information about license you can found on owners sites.
How do I access the free Forensic Toolkit download for PC?
It's easy! Just click the free Forensic Toolkit download button at the top left of the page. Clicking this link will start the installer to download Forensic Toolkit free for Windows.
Will this Forensic Toolkit download work on Windows?
Yes! The free Forensic Toolkit download for PC works on most current Windows operating systems.
Screenshots
More info
- Developer:Accessdata Group
- File size:4.7MB
- Operating system:Windows 10, Windows 8/8.1, Windows 7, Windows Vista, Windows XP
Related Apps
Specialized Tools
Specialized Tools
Specialized Tools
